Around 3 years ago I revamped planet.gnu.org and hosted it myself, as the previous host was defunc.
I won't have the energy host it for much longer, so planet.gnu.org is now looking for a new host and maintainer.
In any case I'll shut down the service when I upgrade to Debian 11 "bullseye" in a few months.
Everything needed to run the service is documented and stored in the infra and config repositories, there is no private data. A previous blog post discusses upcoming tasks. The planet@gnu.org contact point is now managed by GNU's Mailman instance. The DNS alias is managed by the FSF sysadmins.
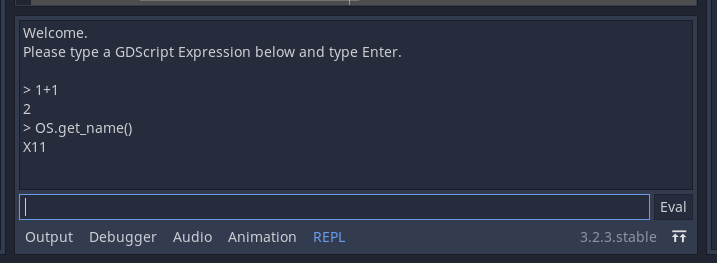
When experimenting with Godot and its GDScript language, I realized that I missed a good old REPL (Read-Eval-Print Loop) to familiarize myself with the language and API.
This is now possible with this new Godot Editor plugin 
Android Rebuilds provides freely-licensed builds of Android development tools from a Mountain View-based company.
Proprietary binaries are rebuilt from source, build recipes are reverse-engineered.
SDK 11 (API 30) is mostly available, as unattended Docker build scripts, build documentation as well as convenience binaries.
Only the x86 system image currently fails to build.
Android Rebuilds provides freely-licensed builds of Android development tools from a Mountain View-based company.
The Emulator package moved to a separate component and build system.
Emulator 30 is now available, as unattended Docker build scripts, build documentation as well as convenience binaries.
I'm mirroring and reworking a large Git repository with git filter-branch (conversion ETA: 20h), and I was wondering how to use --state-branch which is supposed to speed-up later updates, or split a large conversion in several updates.
The documentation is pretty terse, the option can produce weird results (like an identity mapping that breaks all later updates, or calling the expensive tree-filter but discarding the results), wrappers are convoluted, but I got something to work so I'll share 
The main point is: run the initial script and the later updates in the same configuration, which means the target branch needs to be reset to the upstream branch each time, before it's rewritten again by filter-branch. In other words, don't re-run it on the rewritten branch, nor attempt some complex merge/cherry-pick.
git fetch
git branch --no-track -f myrewrite origin/master
git filter-branch \
--xxx-filter ... \
--xxx-filter ... \
--state-branch refs/heads/filter-branch/myrewrite \
-d /dev/shm/filter-branch/$$ -f \
myrewrite
Updates restart from scratch but only take a few seconds to skim through all the already-rewritten commits, and maintain a stable history.
Note that if the process is interrupted, the state-branch isn't modified, so it's not a stop/resume feature. If you want to split a lenghty conversion, you could simulate multiple upstream updates by checking out successive points in history (e.g. per year using $(git rev-list -1 --before='2020-01-01 00:00:00Z')).
--state-branch isn't meant to rewrite in reverse chronological order either, because all commit ids would constantly change. Still, you can rewrite only the recent history for a quick discardable test.
Be cautious when using/deleting rewritten branches, especially during early tests, because Git tends to save them to multiple places which may desync (e.g. .git/refs/heads/, .git/logs/refs/, .git/packed-refs). Also remember to delete the state-branch between different tests. Last, note the unique temporary directory -d to avoid ruining concurrent tests ^_^'
Here is my transparent report for my work on the Debian Long Term Support (LTS) and Debian Extended Long Term Support (ELTS), which extend the security support for past Debian releases, as a paid contributor.
In September, the monthly sponsored hours were split evenly among contributors depending on their max availability - I was assigned 19.75h for LTS (out of my 30 max; all done) and 20h for ELTS (out of my 20 max; all done).
ELTS - Jessie
- qemu: jessie triage: finish work started in August
- qemu: backport 5 CVE fixes, perform virtual and physical testing, security upload ELA-283-1
- libdbi-perl: global triage: clarifications, confirm incomplete and attempt to get upstream action, request new CVE following discussion with security team
- libdbi-perl: backport 5 CVE fixes, test, security upload ELA-285-1
LTS - Stretch
- qemu: stretch triage, while working on ELTS update; mark several CVEs unaffected, update patch/status
- wordpress: global triage: reference new patches, request proper CVE to fix our temporary tracking
- wordpress: revamp package: upgrade to upstream's stable 4.7.5->4.7.18 to ease future updates, re-apply missing patches, fix past regression and notify maintainer, security upload DLA-2371-1
- libdbi-perl: common work with ELTS, security upload DLA-2386-1
- public IRC team meeting
Documentation/Scripts
- LTS/TestSuites/wordpress: new page with testsuite import and manual tests
- LTS/TestSuites/qemu: minor update
- wiki.d.o/Sympa: update Sympa while using it as a libdbi-perl reverse-dep test (update for newer versions, explain how to bootstrap admin access)
- www.d.o/lts/security: import a couple missing announcements and notify uploaders about procedures
- Check status for pdns-recursor, following user request
- Check status for golang-1.7 / CVE-2019-9514 / CVE-2019-9512
- Attempt to improve cooperation after seeing my work discarded and redone as-is, which sadly isn't the first time; no answer
- Historical analysis of our CVE fixes: experiment to gather per-CVE tracker history
Here is my transparent report for my work on the Debian Long Term Support (LTS) and Debian Extended Long Term Support (ELTS), which extend the security support for past Debian releases, as a paid contributor.
In August, the monthly sponsored hours were split evenly among contributors depending on their max availability - I was assigned 21.75h for LTS (out of my 30 max; all done) and 14.25h for ELTS (out of my 20 max; all done).
We had a Birds of a Feather videoconf session at DebConf20, sadly with varying quality for participants (from very good to unusable), where we shared the first results of the LTS survey.
There were also discussions about evaluating our security reactivity, which proved surprisingly hard to estimate (neither CVE release date and criticality metrics are accurate nor easily available), and about when it is appropriate to use public naming in procedures.
Interestingly ELTS gained new supported packages, thanks to a new sponsor -- so far I'd seen the opposite, because we were close to the EOL.
As always, there were opportunities to de-dup work through mutual cooperation with the Debian Security team, and LTS/ELTS similar updates.
ELTS - Jessie
- Fresh build VMs
- rails/redmine: investigate issue, initially no-action as it can't be reproduced on Stretch and isn't supported in Jessie; follow-up when it's supported again
- ghostscript: global triage: identify upstream fixed version, distinguish CVEs fixed within a single patch, bisect non-reproducible CVEs, reference missing commit (including at MITRE)
- ghostscript: fix 25 CVEs, security upload ELA-262-1
- ghostscript: cross-check against the later DSA-4748-1 (almost identical)
- software-properties: jessie triage: mark back for update, at least for consistency with Debian Stretch and Ubuntu (all suites)
- software-properties: security upload ELA-266-1
- qemu: global triage: update status and patch/regression/reproducer links for 6 pending CVEs
- qemu: jessie triage: fix 4 'unknown' lines for qemu following changes in package attribution for XSA-297, work continue in September
LTS - Stretch
- sane-backends: global triage: sort and link patches for 7 CVEs
- sane-backends: fix dep-8 test and notify the maintainer,
- sane-backends: security upload DLA-2332-1
- ghostscript: security upload DLA 2335-1 (cf. common ELTS work)
- ghostscript: rebuild ("give back") on armhf, blame armhf, get told it was a concurrency / build system issue -_-'
- software-properties: security upload DLA 2339-1 (cf. common ELTS work)
- wordpress: global triage: reference regression for CVE-2020-4050
- wordpress: stretch triage: update past CVE status, work continues in September with probably an upstream upgrade 4.7.5 -> 4.7.18
- nginx: cross-check my July update against the later DSA-4750-1 (same fix)
- DebConf BoF + IRC follow-up
Documentation/Scripts
- Clarify/link salsa:lts-team/lts-extra-tasks against salsa:freexian-team/project-funding (description)
- Historical analysis of our CVE fixes: check feasibility
- webwml:find-missing-advisories: handle missing trailing slash, print DSA/DLA date, print affected package rather than committer
- discussion on public naming (shaming?)
- LTS/TestsSuites/sane-backends: test with more complex DEP-8/autopkgtest setup
The system running planet.gnu.org was upgraded/reinstalled to Debian 10 "buster" 
Documentation was updated.
Let me know if you notice any issue - planet@gnu.org.
For the next upgrade, we'll have to decide whether to takeover Planet Venus and upgrade it to Python 3, or migrate to another Planet software.
Suggestions/help welcome 
Here is my transparent report for my work on the Debian Long Term Support (LTS) and Debian Extended Long Term Support (ELTS), which extend the security support for past Debian releases, as a paid contributor.
In July, the monthly sponsored hours were split evenly among contributors depending on their max availability - I was assigned 25.25h for LTS (out of 30 max; all done) and 13.25h for ELTS (out of 20 max; all done).
We shifted suites: welcome Stretch LTS and Jessie ELTS. The LTS->ELTS switch happened at the start of the month, but the oldstable->LTS switch happened later (after finalizing and flushing proposed-updates to a last point release), causing some confusion but nothing major.
ELTS - Jessie
- New local build setup
- ELTS buildds: request timezone harmonization
- Reclassify in-progress updates from jessie-LTS to jessie-ELTS
- python3.4: finish preparing update, security upload ELA 239-1
- net-snmp: global triage: bisect CVE-2019-20892 to identify affected version, jessie/stretch not-affected
- nginx: global triage: clarify CVE-2013-0337 status; locate CVE-2020-11724 original patch and regression tests, update MITRE
- nginx: security upload ELA-247-1 with 2 CVEs
LTS - Stretch
- Reclassify in-progress/needed updates from stretch/oldstable to stretch-LTS
- rails: upstream security: follow-up on CVE-2020-8163 (RCE) on upstream bug tracker and create pull request for 4.x (merged), hence getting some upstream review
- rails: global security: continue coordinating upload in multiple Debian versions, prepare fixes for common stretch/buster vulnerabilities in buster
- rails: security upload DLA-2282 fixing 3 CVEs
- python3.5: security upload DLA-2280-1 fixing 13 pending non-critical vulnerabilities, and its test suite
- nginx: security upload DLA-2283 (cf. common ELTS work)
- net-snmp: global triage (cf. common ELTS work)
- public IRC monthly team meeting
- reach out to clarify the intro from last month's report, following unsettled feedback during meeting
Documentation/Scripts
- ELTS/README.how-to-release-an-update: fix typo
- ELTS buildd: attempt to diagnose slow perfs, provide comparison with Debian and local builds
- LTS/Meetings: improve presentation
- SourceOnlyUpload: clarify/de-dup pbuilder doc
- LTS/Development: reference build logs URL, reference proposed-updates issue during dists switch, reference new-upstream-versioning discussion, multiple jessie->stretch fixes and clean-ups
- LTS/Development/Asan: drop wheezy documentation
- Warn about jruby mis-triage
- Provide feedback for ksh/CVE-2019-14868
- Provide feedback for condor update
- LTS/TestsSuites/nginx: test with new request smuggling test cases
Here is my transparent report for my work on the Debian Long Term Support (LTS) and Debian Extended Long Term Support (ELTS), which extend the security support for past Debian releases, as a paid contributor.
In June, the monthly sponsored hours were split evenly among contributors depending on their max availability - I was assigned 30h for LTS (out of 30 max; all done) and 5.25h for ELTS (out of 20 max; all done).
While LTS is part of the Debian project, fellow contributors sometimes surprise me: suggestion to vote for sponsors-funded projects with concorcet was only met with overhead concerns, and there were requests for executive / business owner decisions (we're currently heading towards consultative vote); I heard concerns about discussing non-technical issues publicly (IRC team meetings are public though); the private mail infrastructure was moved from self-hosting straight to Google; when some got an issue with Debian Social for our first video conference, there were immediate suggestions to move to Zoom...
Well, we do need some people to make those LTS firmware updates in non-free 
Also this was the last month before shifting suites: goodbye to Jessie LTS and Wheezy ELTS, welcome Stretch LTS and Jessie ELTS.
ELTS - Wheezy
- mysql-connector-java: improve testsuite setup; prepare wheezy/jessie/stretch triple builds; coordinate versioning scheme with security-team; security upload ELA 234-1
- ntp: wheezy+jessie triage: 1 ignored (too intrusive to backport); 1 postponed (hard to exploit, no patch)
- Clean-up (ditch) wheezy VMs

LTS - Jessie
- mysql-connector-java: see common work in ELTS
- mysql-connector-java: security uploads DLA 2245-1 (LTS) and DSA 4703 (oldstable)
- ntp: wheezy+jessie triage (see ELTS)
- rails: global triage, backport 2 patches, security upload DLA 2251-1
- rails: global security: prepare stretch/oldstable update
- rails: new important CVE on unmaintained 4.x, fixes introduce several regressions, propose new fix to upstream, update stretch proposed update [and jessie, but rails will turn out unsupported in ELTS]
- python3.4: prepare update to fix all pending non-criticial issues, 5/6 ready
- private video
^W^Wpublic IRC team meeting
Documentation/Scripts
- LTS/TestsSuites/mysql-connector-java: improve testsuite setup for better coverage
- LTS/TestSuites/tiff: document package maintainer's (extensive) tests
- LTS/TestSuites/rails: first version
- LTS/TestSuites/python: how to run individual test
- LTS/Development: clarifications on grouping fixes and validating patches
- internal discussion on (not) capping LTS-funded hours
- discussion on unbound and freerdp EOL
- tzdata, libdatetime-timezone-perl: check and explain delayed update workflow
- ELTS: update new tracker URL in documentation
This blog is powered by ikiwiki.